As ecommerce continues to grow in popularity, so has the threat of ecommerce fraud and money laundering cybercrimes. Payment service providers can be the first line of defense against money laundering by playing an important role in anti-money laundering (AML) strategies, like identifying risk through sophisticated fraud technology, having comprehensive and rigorous know your customer (KYC) infrastructures, and having ongoing consultations with merchants to ensure that your business, and customers, are educated and protected.
What is AML transaction monitoring?
Companies use anti-money laundering (AML) transaction monitoring to detect and prevent money laundering and terrorist financing. They do this by using software to assess transfers, deposits and withdrawals for suspicious patterns or signs that might indicate criminal activity.
To meet AML transaction monitoring requirements, your business must conduct checks on any transaction that passes the thresholds set by your regulatory body. These thresholds vary by country and sector. You’re also required to check transactions and customers against lists of sanctions and politically exposed persons (PEPs).
How does AML transaction monitoring work?
Real-time AML transaction monitoring systems use machine learning and risk-based rules to analyze data from every single transaction, deposit or withdrawal. You can customize the rules your system uses to automatically flag any transaction that passes certain thresholds or that bears suspicious characteristics. If a transaction is flagged, it can be automatically sent for review.
Suspicious activity can include unusually large movements of money, frequent and unexplained transfers between accounts, or activity that is atypical of a particular customer.
If, upon further investigation, you know or suspect your customer to be involved in money laundering, you’re required to submit a Suspicious Activity Report (SAR) to your regulatory authority. A compliance agent will use this information to investigate further.
Whether they’re suspicious or not, you must keep a record of all transactions, including the type, amount and date, as well as records of the customers involved. This provides an audit trail and serves as crucial evidence in the event that one of your customers is investigated.
Understanding anti-money laundering (AML)
AML refers to the laws and procedures used to identify and prevent money laundering, the process criminals use to disguise the origin of illicit funds by funneling them through legitimate systems and businesses.
To prevent this, AML regulations require any organization that falls under their jurisdiction to conduct Know Your Customer (KYC) checks on new clients in order to verify their identity, and to monitor their transactions for any activity that could be evidence of money laundering.
AML is enforced by different regulatory bodies in different countries. In the UK, for example, the Financial Conduct Authority (FCA) is responsible for ensuring firms comply with AML regulations. These regulations vary from country to country, but generally speaking, AML applies to all businesses operating in industries where there’s a high risk of money laundering, such as financial services, real-estate, accountancy, and the art market.
Money laundering is one of the most common types of financial fraud. Illicit drugs, online gambling, counterfeit goods and adult content account for nearly 50-70% of transaction laundering, according to a report by Thomson Reuters on the growing threat of money laundering. In a 2018 report, fake merchants made up $352 billion in laundered money annually in the U.S. alone.
What are some examples of money laundering?
The most common type of online money laundering is transaction laundering and occurs in 3 main forms:
- Front companies, which use legitimate businesses as a cover for criminal activities.
- Pass-through companies, which allow illegal businesses to process credit cards through their legitimate business by allowing access to their payments processing account.
- Funnel accounts, which are legal businesses that accept credit card charges from multiple companies that do not have their own merchant payment account due to illegitimate business dealings.
Money laundering typically takes place in three stages. The initial stage is called placement. This is where the criminal introduces their illicit funds into a legitimate financial system. To avoid suspicion, they will often split large sums of illegally-gained money into smaller sums and then use them for different purposes.
The second stage of money laundering is called layering. Layering involves blending illicit cash with legitimate cash by using it to make multiple transactions or moving it through a series of different bank accounts.
The final stage of money laundering is ‘integration’, where they will pass the money through a variety of channels at which point the illegally obtained funds will appear “clean.” One common integration method is selling e-vouchers on marketplaces or auction sites where the clean funds are now in the wallet, bank transfer, or is cashed. Another method is to convert the money into cryptocurrency where it disappears off the radar; once cryptocurrency is sold, the funds from the sale become extremely difficult to trace back to the original source.
What is driving money laundering in online transactions?
According to PWC, Cybercrime is the most common type of fraud experienced by businesses of up to $10bn in revenue, especially in tech and media, health, and manufacturing. Of businesses that had experienced fraud in the last two years, 40% said it was connected to the platforms they rely on, whether related to KYC breaches, money laundering, or terrorism financing.
But why? The advent of advanced digital technologies has given criminals new ways to launder their money, sometimes known as cyberlaundering. Regulations and security standards for new technologies aren’t always as developed as those used by established financial institutions, meaning there are more loopholes and opportunities for criminals to exploit. Additionally, the growing use of encryption tools like VPNs, and the use of multiple digital systems for each stage of laundering can make criminal activity almost impossible to trace.
For example, mobile wallet payments now account for nearly half (49%) of all global ecommerce payment transactions, yet the anonymity and ease of the technology lends itself to money laundering. Firstly, it’s easy for someone to set up multiple different accounts under false names and make quick transfers and withdrawals all from their smartphone, without the need to ever have a face-to-face interaction. Secondly, as the fees for mobile payments are often lower than with traditional banks, the costs of splitting up large sums is much cheaper, making it an attractive way to conduct placement. Virtual currencies like bitcoin are also an exciting prospect for cybercriminals as they allow for anonymous and untraceable transactions.
As the ecommerce landscape continues to embrace emerging technologies in 2023 and beyond, regulators and businesses will have to be vigilant about how cybercriminals might seek to exploit weaknesses in the systems and platforms they use.
Learn more: Synthetic identity fraud
What is the difference between transaction monitoring and screening in AML?
Transaction monitoring and screening are both procedures that businesses need to implement to comply with AML. Both play a crucial role in the fight against money laundering, but what’s the difference and how do they relate to other procedures such as KYC and CDD? Let’s look a some definitions:
- Transaction monitoring - the use of software to monitor transactions in order to detect suspicious account activity, such as unusually large deposits or frequent transfers. If transactions pass certain thresholds set by regulatory bodies, they should be investigated and, if necessary, reported with an SAR
- Screening - the process of conducting checks on customers, including verifying identities, sanctions and PEP checks, and crime and watchlist screening. This is done in order to establish whether there’s a possibility that the customer is involved in money laundering
- KYC - Know Your Customer (KYC) is a set of standards used to verify the identity of new clients and to understand their risk and financial profiles during onboarding
- CDD - Customer Due Diligence (CDD) is a part of the KYC process that assesses the client’s risk profile throughout the business-client relationship. It involves the collection and verification of credentials and ongoing monitoring of their activities
What AML processes should businesses have to combat money laundering?
Businesses that fall under the scope of AML should ensure they have sufficient policies, procedures, training and technologies in place to comply. That means meeting any requirements stipulated by AML by implementing the following processes:
- Onboarding - proper KYC-compliant onboarding requires you to collect and verify all necessary documentation, understand the nature of their activities and assess their risk of money laundering
- Ongoing monitoring - ongoing monitoring, required for KYC/CDD, should involve continual assessment of your client, including recording communications and transactions and changes of status, and looking out for suspicious activity
- Restricting transactions, deposits and withdrawals - this should be done in order to ensure criminals aren’t able to move money around too easily and frequently. They do this during the layering stage of laundering in an attempt to disguise its illicit origin
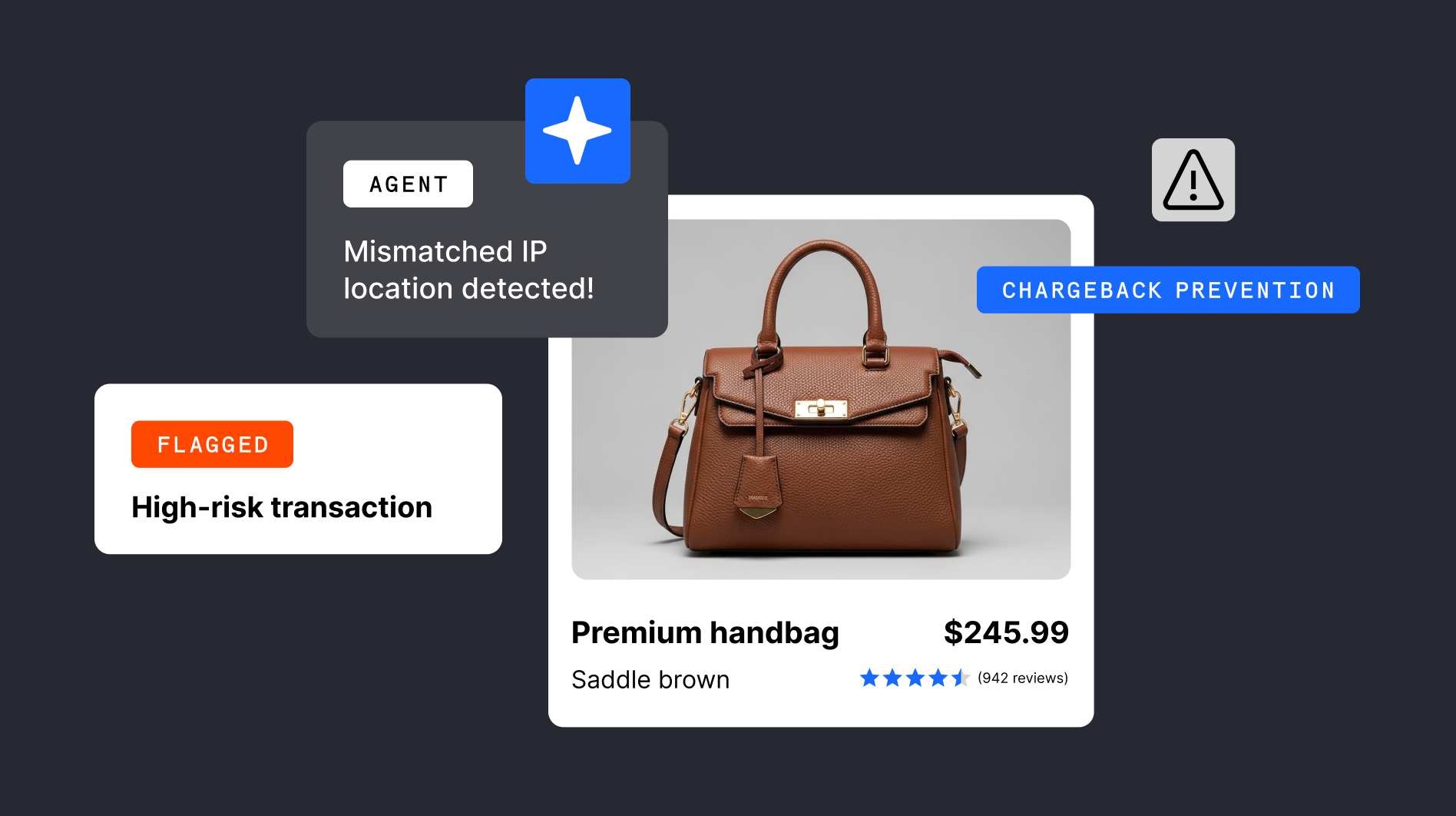
- Adopt fraud detection technology - which learns to identify suspicious activity such as unusually large transactions, a high volume of transactions, or transactions involving individuals or jurisdictions with a history of money laundering. These transactions can then be automatically routed for blocking, review, or further authentication. You can do this by partnering with a PSP like Checkout.com. Our Fraud Detection solution uses machine learning to stay on top of fraudulent trends, and to identify and block fraud as it's happening
Individuals working in the financial sector, professional services and high-value retainers, assume a criminal liability for failing to report suspicious transactions, so it’s in their best interest to have checks in place and are enforced regularly.
As companies continue to build new products and features designed for user-friendliness and frictionless experiences, they must also stay a step ahead and consider all fraud implications with their releases. And early-stage companies, who may be eager for business at the onset, have to be particularly careful and set a precedence early on in order to ensure success in the long run.
How to choose the best AML monitoring solution?
When deciding on the best AML monitoring solution for your business, you should look for a system that has the following capabilities:
- Velocity rules - velocity rules allow you to monitor and trigger actions based on the frequency of transactions with matching attributes over a specific period, which could be daily, weekly, or monthly. They are especially useful for spotting suspicious activity. For example, you could trigger your system to flag when a customer’s transactions exceed a certain dollar amount within a day
- Real-time monitoring - real-time transaction monitoring is essential to keep up with the rapid pace of online money laundering. It uses AI to automatically monitor customer activity far more effectively than manual processes and can immediately block transactions if they display suspicious characteristics
- Custom rules - you can use custom rules to create highly specific triggers depending on your risk strategy. For example, you could create a rule that triggers when the same customer attempts to pay with three different cards in one hour
- Machine learning (thresholds) - machine learning scores the risk level of a transaction from one to 100. If the transaction score is over a threshold of say, 70, the transaction will be flagged as having a high probability of being fraudulent
- Tokenization - tokenization replaces sensitive data with a unique token that can be used during financial transactions without making that data vulnerable to criminals
How to set up an AML transaction monitoring process with Checkout.com?
With Checkout.com’s Fraud Detection Pro solution, you have all the tools you need to identify and prevent potential money laundering activity, and to meet your AML requirements.
Using velocity rules and custom rules, you can build a tailored risk strategy that automatically logs, blocks or routes transactions for manual review if they meet certain conditions.
So, for example, you can create a rule that logs transfers over $3,000, meeting your requirement to record any transaction over this amount under US AML laws. Or, you could create a velocity rule that spots when a customer’s transaction volume increases by 500% in a week, or whatever time-frame and percentage aligns with your strategy. If the rule is triggered, you can decide to add a certain number of points to their fraud score, indicating that they now present an increased level of risk.
Meanwhile, our advanced machine learning detects fraudulent trends from across our entire network to stay ahead of the criminals.
Want to learn more about how Checkout.com can help protect your business? Get in touch with our payments and fraud experts today for more information.











.png)
