Frictionless authentication plays an important role in online transactions, the customer journey and fraud prevention techniques. But what is it and how does it work?
This page will explain everything you need to know about frictionless authentication, including its techniques, benefits and potential drawbacks. We’ll also explain how, as the world’s first 3DS 3.2.1 certified end-to-end payment provider, Checkout.com can help your business employ frictionless authentication techniques.
What is frictionless authentication?
Frictionless authentication is an automated identity verification approach centered on risk assessment. Its primary objective is to facilitate access for legitimate users while deterring risky ones, all while minimizing the need for the user to provide personal information.
The fundamental principle of frictionless authentication is that user identification occurs in real-time without hindering the overall customer journey. This seamless authentication method can be implemented during various digital processes such as onboarding, login, or transactions.
In contrast, high-friction authentication methods may include protocols like selfie video verification, multi-factor authentication, document uploads, manual form reviews, and CVV and address verification for payments.
By eliminating high-friction steps, your business can employ frictionless authentication. However, this carries the risk of potentially allowing more fraudulent actions from malicious users. That’s why it’s so important to strike the right balance between safety and user convenience.
How Does Frictionless Authentication Work?
For the frictionless flow, the approval of a transaction depends on the 3D Secure protocol's evaluation of the transaction's risk factor. The 3D Secure protocol employs a range of risk-based assessments to thoroughly analyze each transaction and decide if additional authentication is necessary.
These risk-based assessments encompass factors like:
- Customer status (new or existing)
- Total transaction value
- Device information
- Transaction history
- Behavior history
Both the merchant and the issuer can utilize these data elements to assess whether the transaction requires further authentication through the 3D Secure protocol.
3D Secure serves as a robust method to ensure the security of online payments by employing multiple layers of protection, safeguarding businesses and customers from fraudulent activities. One of these protective layers is referred to as "frictionless authentication," which alleviates the burden of memorizing numerous passwords.
Instead of using passwords, 3D Secure leverages a combination of the customer's device, browser, and the 3D Secure SDK to verify their identity. This approach aims to maintain a seamless and user-friendly experience for customers while upholding a high standard of security.
Continuously evolving, 3D Secure stays one step ahead of fraudsters to provide the utmost level of protection and an unparalleled experience for its users.
Frictionless authentication techniques
There are many ways your business can implement smooth, reliable authentication, including:
3D Secure (3DS)
When a customer initiates an online payment, the 3DS technology assesses whether additional security measures are necessary to verify their identity as the rightful card owner. If required, they’ll be redirected to a 3DS page where they’ll be prompted to provide a password or PIN.
At the same time, the customer’s bank generates a unique, one-time PIN and delivers it to their email, or mobile phone via SMS. This PIN serves as the key the customer must enter before finalizing the transaction, ensuring enhanced security and authentication.
In fact, Checkout.com is the first end-to-end payments provider to be 3DS 2.3.1 certified.
Token based (authentication apps, SMS codes, one-time passwords (OTP))
An authentication token serves as a secure conduit for transmitting user identity information between various applications and websites, empowering businesses to bolster their authentication processes for these services.
With an authentication token, internet users can effortlessly access applications, services, websites, and APIs without the need to repeatedly enter their login credentials. Upon the initial login, a distinct token is generated and shared with interconnected applications or websites to authenticate the user's identity.
Think of these tokens like digital stamped tickets for an event. The user, or bearer of the token, is granted access to a website until they log out or terminate the service, similar to holding an access token for the duration of their session.
Learn more: 2FA vs MFA
Biometric authentication
Biometric authentication is a cybersecurity method that confirms a user's identity by using their distinct biological characteristics, such as fingerprints, voices, retinas, and facial features. These unique traits are stored within biometric authentication systems, enabling verification of a user's identity when they attempt to access their account.
Facial recognition
A facial recognition system employs biometrics to analyze facial features extracted from a photograph or video. By comparing this information with a database of known faces, the system seeks to find a match and verify a person's identity. While facial recognition can be beneficial for identity verification, it also raises significant privacy concerns.
QR codes
QR code authentication represents a phone-as-a-token authentication method utilized for user identification. In this approach, traditional QR codes play a vital role in enabling your business to implement multi-factor authentication for its users, generating a time-based one-time password (TOTP), adding an extra layer of security to the authentication process.
Device recognition
Device recognition technology serves the purpose of identifying and acknowledging each network-connected device while gathering comprehensive data about them, including manufacturer, model, and operating system. This valuable information proves beneficial for various IT applications, particularly cybersecurity.
Having constant awareness of the devices connected to the network facilitates swift and effective security threat investigations and remediation. Moreover, it contributes to enhancing overall IT management and optimization efforts. The rich data obtained through device recognition technology proves to be a valuable asset in safeguarding the network and optimizing its performance.
Risk-based authentication
Risk-based authentication, also known as context-based authentication, involves the verification of a user during the sign-on process and evaluating their score against a predefined set of policies, created by your business. These policies determine whether access to resources should be granted or denied, depending on the perceived level of risk associated with the user's authentication attempt.
SSO single sign on
Single sign-on (SSO) is a technology that consolidates multiple application login screens into a unified interface. By utilizing SSO, a user is required to enter their login credentials (username, password, etc.) only once on a single page, granting them access to all their Software as a Service (SaaS) applications without the need for repetitive logins.
Why is frictionless authentication important?
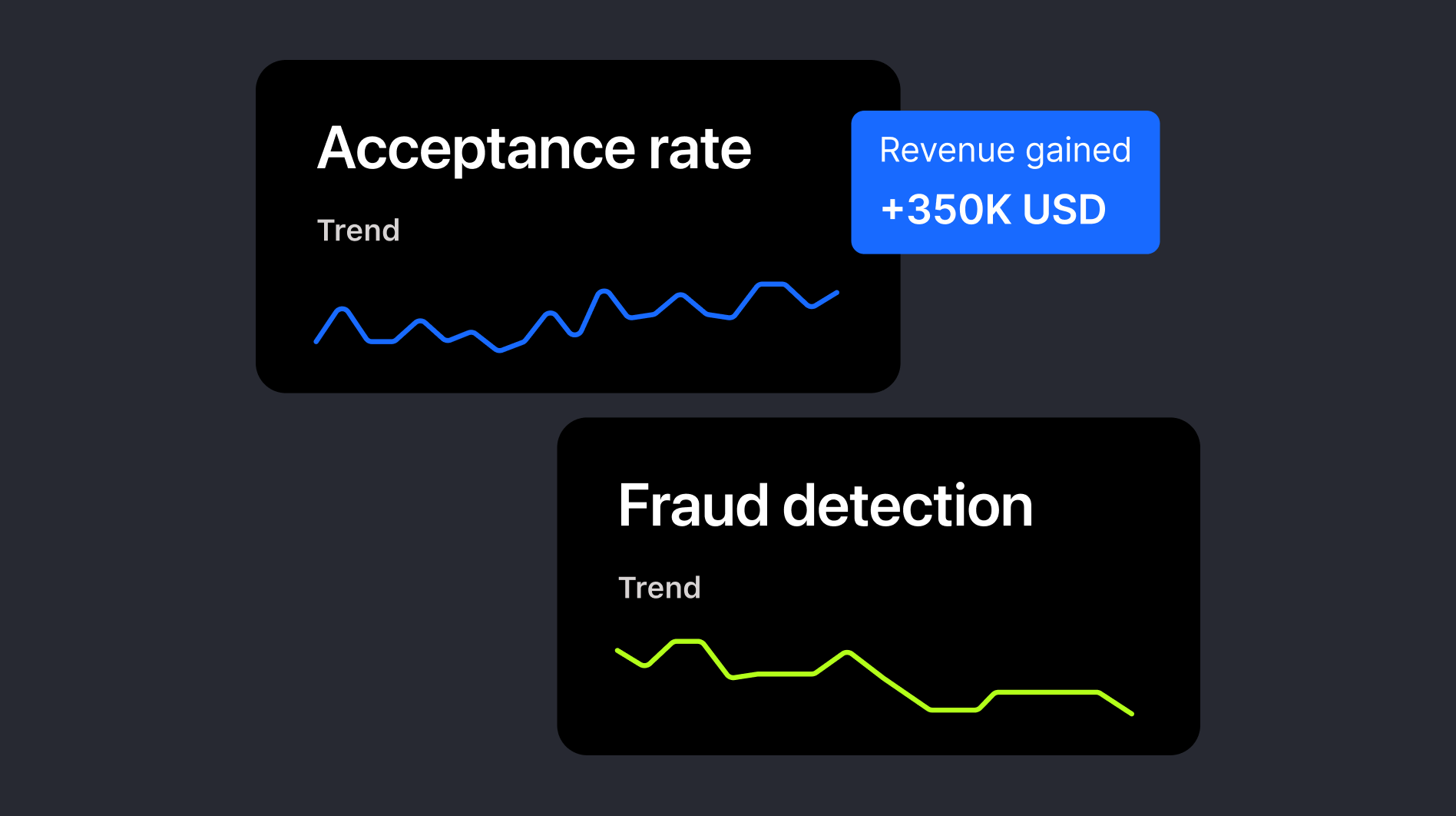
According to 2022 research by the open bank, Tink, 88% of consumers abandon payments if they’re faced with friction. This shows how important it is for your business to accommodate consumer preferences, i.e. provide the fewest number of obstacles, in order to maintain revenue and mitigate lost sales.
In the competitive landscape where customer experience determines the success or failure of businesses, companies are highly motivated to enhance user convenience. Whether it involves facilitating purchases of goods or services, streamlining platform onboarding, or simplifying the login process to access user accounts, providing a seamless and user-friendly experience has become a crucial factor for achieving success.
Difference between frictionless flow vs challenge flow
Customers have two distinct methods to verify themselves through 3D Secure: frictionless and challenge.
In the frictionless flow, background information is used, eliminating the need for customers to actively verify themselves. Also, the SDK and servers handle all essential information exchange without involving the user directly.
In the challenge flow, the issuer has decided that the transaction requires additional verification from the customer.
3D secure and frictionless authentication
During the payment process, 3DS2 enables the merchant and payment providers to transmit over 100 data elements (such as shipping address, device ID, and payment history) to the cardholder's bank to evaluate the transaction's risk level. All of this occurs seamlessly in the background within your web or mobile checkout flow.
Based on the gathered data, the customer's bank will decide whether to authenticate the payment immediately through a frictionless flow or request additional information before proceeding with authentication in a challenge flow.
If the bank deems the data sufficient and trusts that the cardholder is making the payment, the transaction qualifies for frictionless authentication, ensuring a smooth and uninterrupted customer experience.
Learn more: 3DS2.3 - what's new?
Benefits of frictionless authentication
Frictionless authentication offers several key benefits for businesses, including:
- Enhanced user experience – frictionless authentication streamlines the login and verification process, providing a seamless and convenient experience for customers, which in turn boosts satisfaction and engagement.
- Reduced cart abandonment – by minimizing the need for complex authentication procedures, frictionless authentication helps reduce cart abandonment rates during the checkout process, leading to increased conversion rates and revenue.
- Improve customer trust and loyalty – the smooth and hassle-free authentication should instill trust and confidence in your customers, fostering loyalty and encouraging repeat business.
- Mitigated fraud risks – frictionless authentication employs advanced security measures in the background, effectively mitigating fraud risks and safeguarding both your business and customers from potential security breaches.
Challenges of frictionless authentication
Despite its range of benefits, frictionless authentication presents some challenges, particularly in terms of implementation and troubleshooting:
- Implementation complexity – integrating frictionless authentication into the already complex 3D Secure system can be challenging, adding further intricacies to the setup.
- Requirement for 3D Secure-enabled cards – your business needs 3D Secure-enabled cards, posing a challenge for businesses without them because you need to obtain these cards to offer frictionless authentication to customers.
- Troubleshooting difficulties – when issues arise during the authentication process, pinpointing the exact problem can be challenging, especially if your business is unfamiliar with 3D Secure. This can hinder timely resolution of technical problems.
Explore 3D secure with Checkout.com
3D Secure is vital for enabling frictionless authentication. As the first end-to-end payments provider to be 3DS 2.3.1 certified, Checkout.com has what it takes to help your business reduce fraud, boost payment performance and improve customer experiences.
Contact our sales team to find out more about our industry-leading 3D Secure solution today.



.png)

.jpeg)

%20v1.jpg)


.png)

.png)